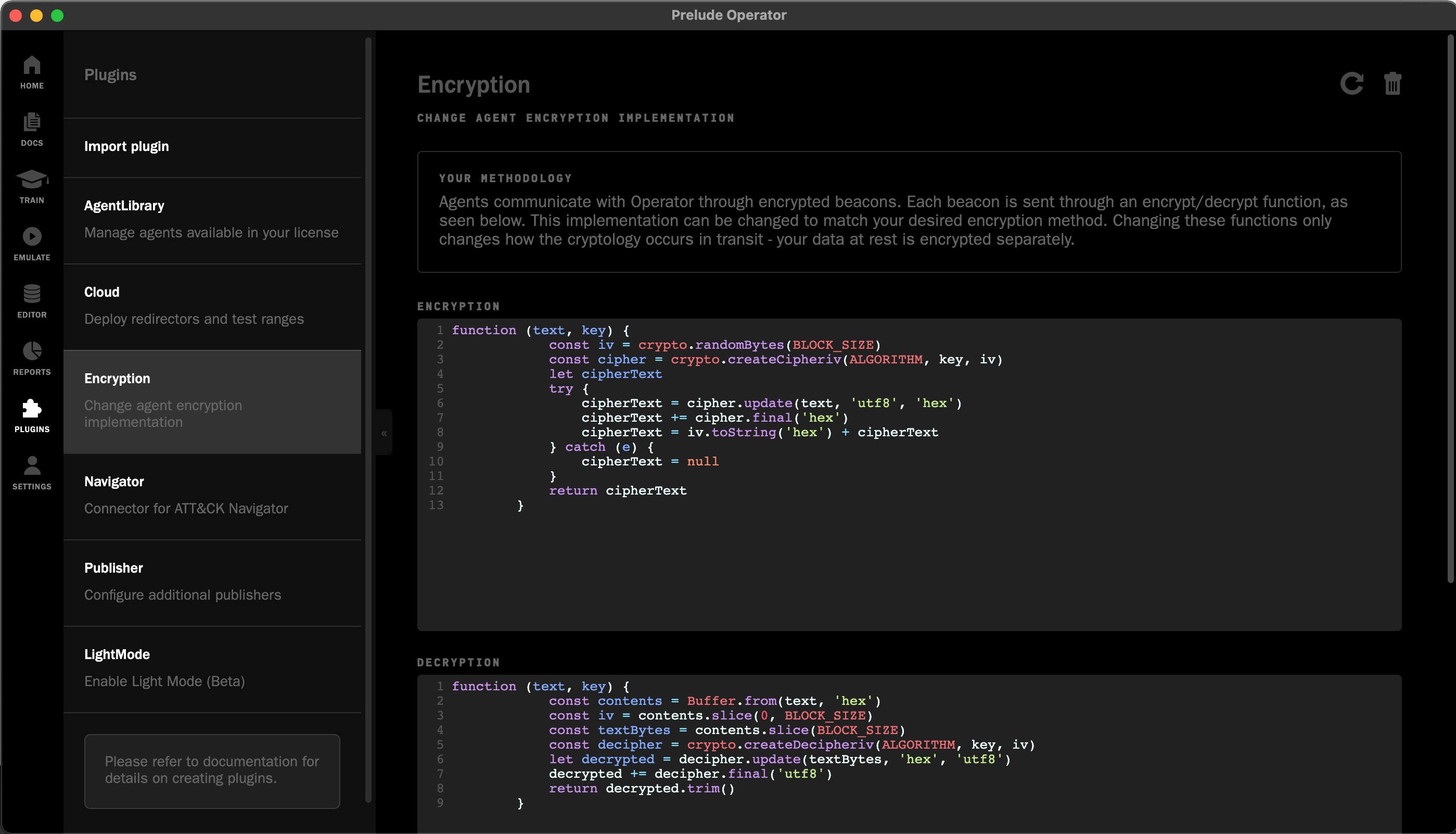
Encrypt and Decrypt users' data in ASP.NET Core Identity using the ILookupProtector and ILookupProtectorKeyRing interfaces - DEV Community

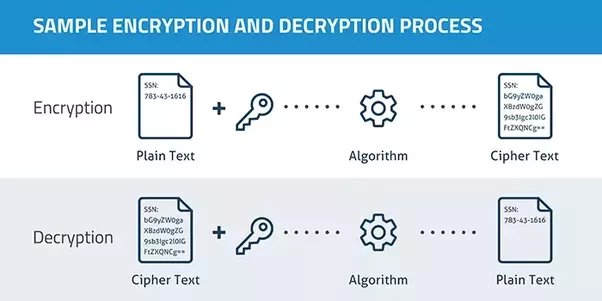
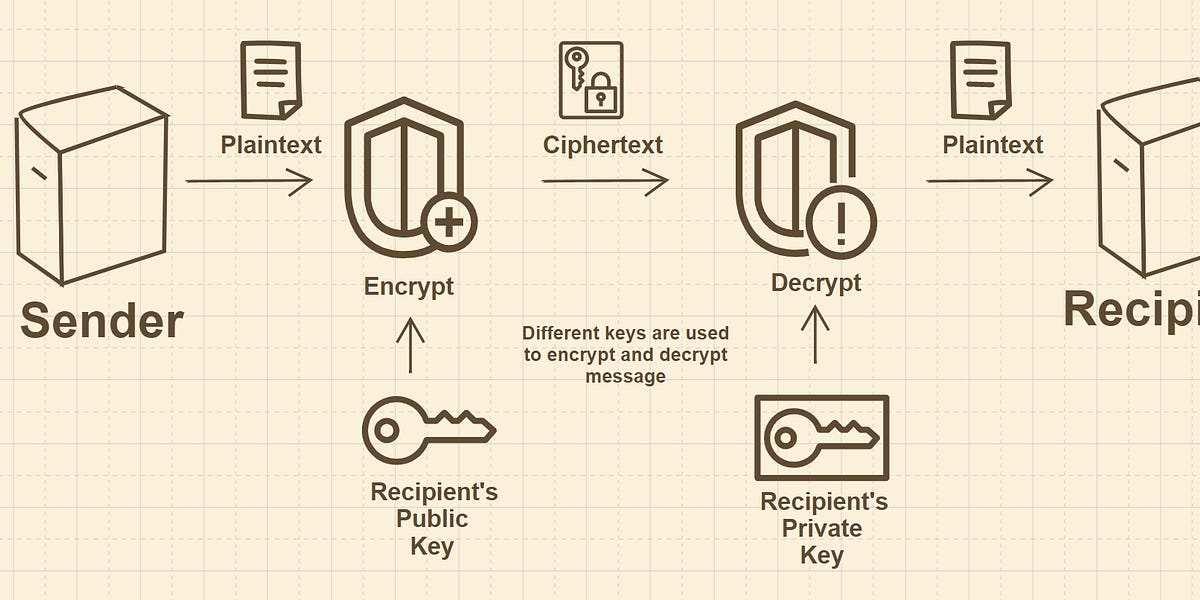
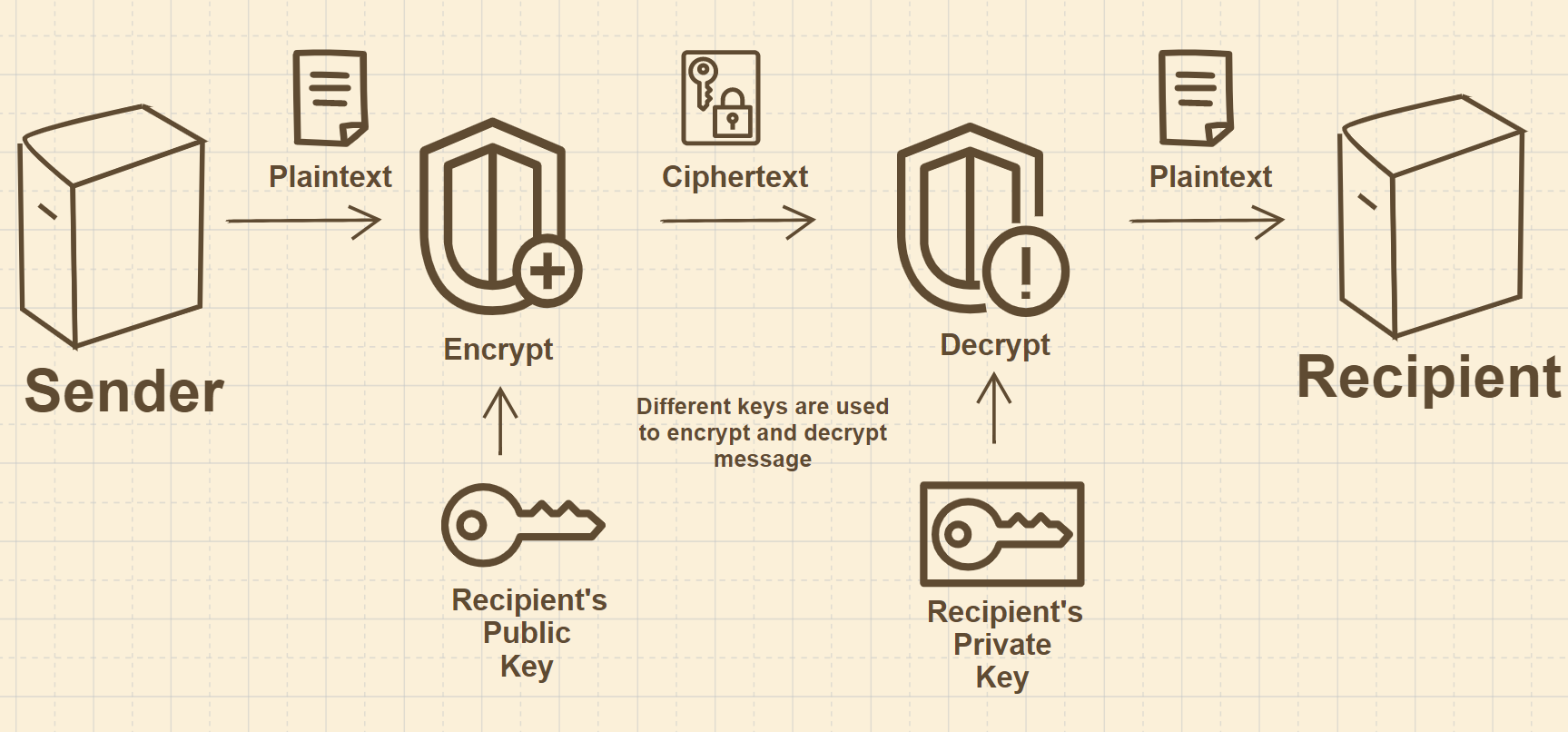
Decrypt the encoded string with help of Matrix as per given encryption decryption technique - GeeksforGeeks

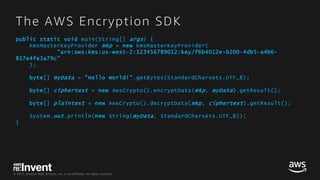
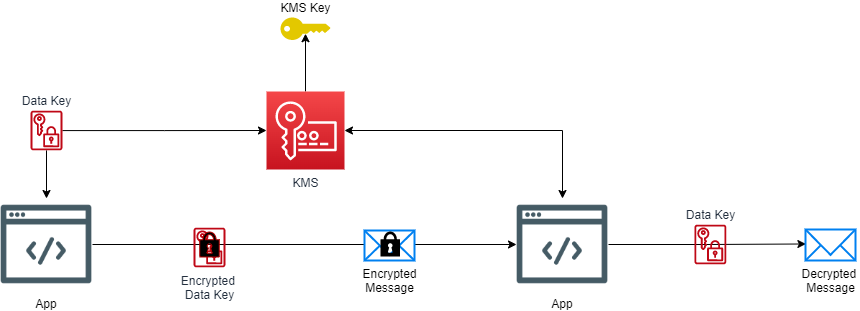
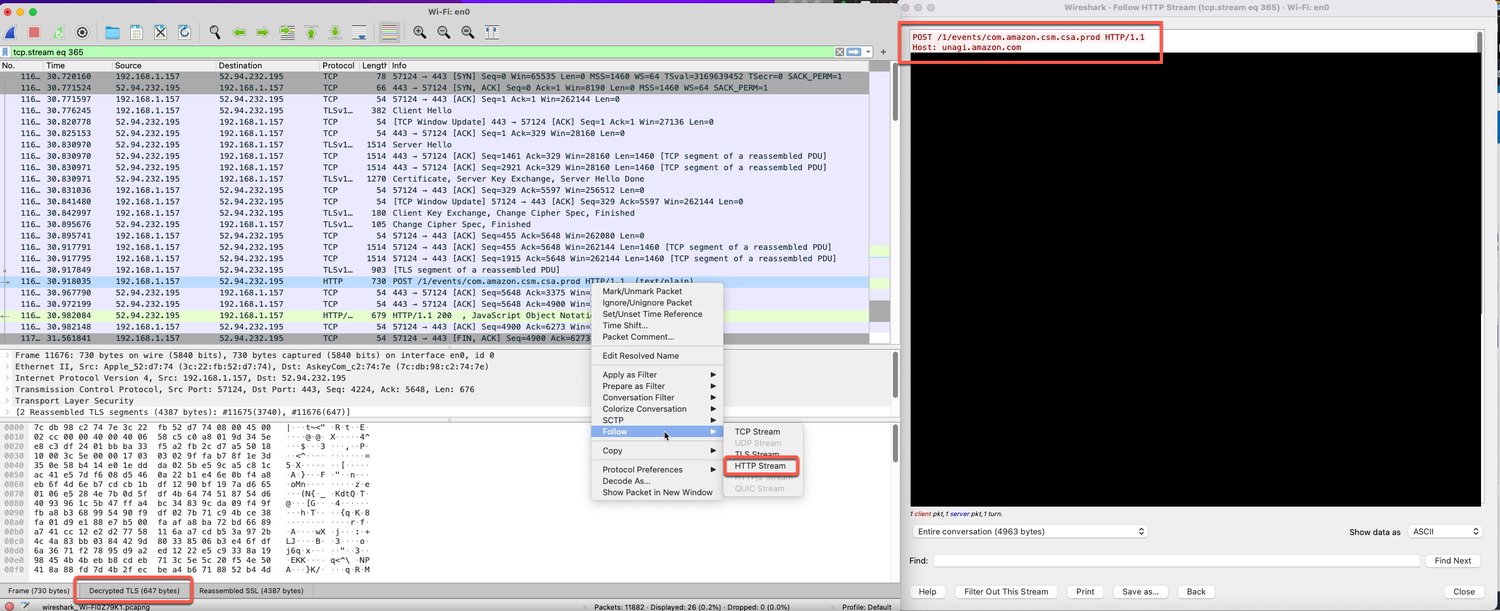
Understanding Amazon DynamoDB encryption by using AWS Key Management Service and analysis of API calls with Amazon Athena | AWS Database Blog